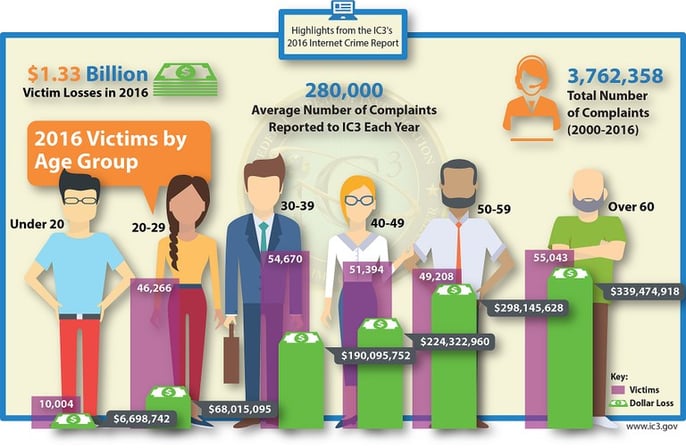
A great article was published today showing highlights of the IC3's 2016 Internet Crime Report. The report, published at www.fbi.gov, included some stastistics and this great visual depicting the victims of internet crime by age group:
The article also includes some sage advice about what you can do to mitigate your chances of falling into one of the categories depicted by the above image. We at Vibato used to receive at least 10 malicious calls a week from someone who is trying to convince us that they need to log into our system because our Microsoft Windows license has expired or that our systems are alerting Microsoft of some issue that they need to help us fix. If it isn't some system scam like that then it's the "IRS" saying they're going to arrest us if we don't send someone a Western Union payment immediately. Oh the joys of having your business phone number published on the internet for all to see...We've stopped answering our phone and instead have an automated dial-by-name directory so the caller is forced to know who they are trying to reach to help mitigate this concern.
As described in the FBI article, "Giving someone access to your computer is like giving out a key to your front door. A computer can have your bank account information, family photos, and other private documents and data—information that fraudsters would like to steal. That’s why tech support fraud has become a significant trend in online crime, according to the 2016 Internet Crime Report from the FBI’s Internet Crime Complaint Center (IC3)."
We encourage you to read the article and take heed. Between the types of callers who try to scare you into letting them on your computer or ransomware and extortion, there are a lot of things to remember and fear when using a computer these days. Education is never a waste and this article can help protect you & your company from a lot of unnecessary heartache.